Introduction
People complain about their internet accounts being “hacked,” but how does this happen? Accounts are hacked in rather straightforward methods; attackers do not use dark magic.
Power comes from knowledge. Understanding how accounts are compromised will assist you in securing your accounts and preventing your passwords from being “hacked” in the first place.
Password Reuse, Especially of Leaked Passwords
Many individuals, if not the majority, repeat passwords across many accounts. Some individuals may even use the same password for all of their accounts. This is exceedingly risky. Many companies, including well-known names like LinkedIn and eHarmony, have had their password databases compromised in recent years. Online databases containing leaked passwords, usernames, and email addresses are widely available. Attackers may utilize these email address, username, and password combinations to gain access to many accounts on other websites.
Reusing a password for your email account puts you even more at danger, since an attacker may use your email account to reset all of your other passwords if they obtain access to it.
You have no influence over how effectively the services you use safeguard your credentials, no matter how skilled you are at securing them. If you reuse passwords and one provider makes a mistake, all of your accounts are at danger. You should use separate passwords for each site – a password manager may assist you with this.
Keyloggers
Keyloggers are malicious programs that may operate in the background and record every keystroke you make. They are often used to get sensitive information such as credit card numbers, internet banking passwords, and other account credentials. They subsequently transmit this information to an attacker through the Internet.
Such malware may infiltrate via vulnerabilities; for example, if you’re running an old version of Java, as most computers on the Internet do, you can be compromised through a Java applet on a web page. They can, however, be concealed in other applications. You could, for example, download a third-party program for an online game. The program might be malicious, collecting your game password and transferring it over the Internet to the attacker.
Use a good antivirus application, maintain your software up to date, and avoid installing dubious software.

Social Engineering
Attackers often utilize social engineering techniques to get access to your accounts.
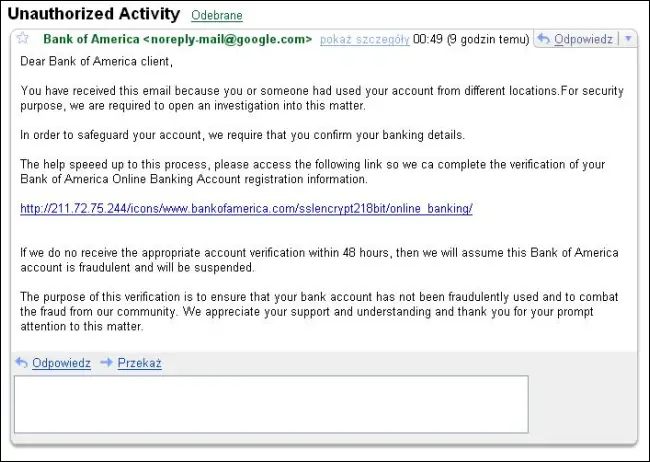
Phishing is a well-known technique of social engineering in which the attacker impersonates someone and requests your password. Some people freely provide away their passwords. The following are some instances of social engineering:
- You get an email purporting to be from your bank, sending you to a bogus bank website with a very similar-looking URL and requesting your password.
- You get a message on Facebook or another social networking site from a person claiming to be an official Facebook account, requesting you to give your password in order to authenticate yourself.
- You go to a website that claims to provide you something useful, such as free Steam games or free World of Warcraft gold. The website wants your login and password for the service in order to get this bogus incentive.
Don’t open links in emails to get to your bank’s website, don’t provide your password to anybody who approaches you and wants it, and don’t give your account information to untrustworthy websites, particularly those that look too good to be true.
Responding to Security Questions
Frequently, passwords may be reset by answering security questions. Security questions are often quite basic, such as “Where were you born?” “What high school did you attend?” and “What was your mother’s maiden name?” This information is often available on publicly accessible social networking sites, and most normal individuals will tell you what high school they attended if asked. Attackers may often change passwords and gain access to accounts using this easily obtained information.
Ideally, you should utilize security questions with difficult-to-find or guess answers. Websites should also prohibit someone from accessing an account just because they know the answers to a few security questions, which some do — but others do not.
Resetting Email Accounts and Passwords
If an attacker utilizes any of the ways listed above to acquire access to your email accounts, you’re in much more danger. In most cases, your email account serves as your primary internet account. All of your other accounts are connected to it, and anybody with access to the email account might use it to change your passwords on any of the sites you enrolled with the email address.
As a result, you should keep your email account as safe as possible. It’s extremely critical to use a unique password for it and to keep it safe.
What Isn’t Password “Hacking”
Most people anticipate attackers attempting every potential password to get access to their internet account. This isn’t going to happen. If you attempted to get into someone’s internet account and kept guessing passwords, you’d be slowed down and barred from attempting more than a few passwords.
If an attacker was able to get access to an online account only by guessing passwords, the password was most likely something simple that could be guessed on the first few attempts, such as “password” or the name of the person’s pet.
Such brute-force techniques could only be used by attackers if they had local access to your data — for example, if you were keeping an encrypted file in your Dropbox account and attackers obtained access to it and downloaded the encrypted file. They may then attempt to brute-force the encryption, effectively attempting every possible password combination until one of them worked.
People who claim their accounts have been “hacked” are most frequently guilty of reusing passwords, installing a key logger, or handing over their credentials to an attacker after falling victim to social engineering methods. They might potentially have been hacked as a consequence of readily known security questions.
It will be difficult to “hack” your accounts if you adopt basic security procedures.
Using two-factor authentication may also assist – an attacker will need more than your password to get access.

